|
What you can not measure, you can not manage!
The Internet of things and services provides the environment for novel applications and processes which may evolve
way beyond pre-planned scope and purpose. Security analysis is growing in complexity with the increase
in functionality, connectivity, and dynamics of current electronic business processes. Technical processes
within critical infrastructures also have to cope with these developments. To tackle the complexity of the
security analysis, the application of models is becoming standard practice. However, model-based support
for security analysis is not only needed in pre-operational phases but also during process execution, in order
to provide situational security awareness at runtime.
|
Predictive Security Analysis (PSA)
An important property of a security metric is its applicability at runtime. A tool-based runtime
calculation of a security metric enables a timely response to attacks as well as an impact mitigation by
triggering appropriate countermeasures. Security information and event management systems provide
security services to collect and analyse security events and data from a wide variety of sources in order
to provide a unified view of the monitored systems' security status. However, an analysis of a
comprehensive set of industrial scenarios has identified several additional security requirements that
are not adequately addressed by current systems.
Thus, we introduced a novel model-based approach for
Predictive Security Analysis at Runtime (PSA@R). In particular, PSA@R widens the focus of the
security analysis from a system level view to the business process level. For effective use of PSA@R, the managed systems need to be designed for security assessment at runtime.
|
"Security@Runtime" supplements "Security-by-Design"
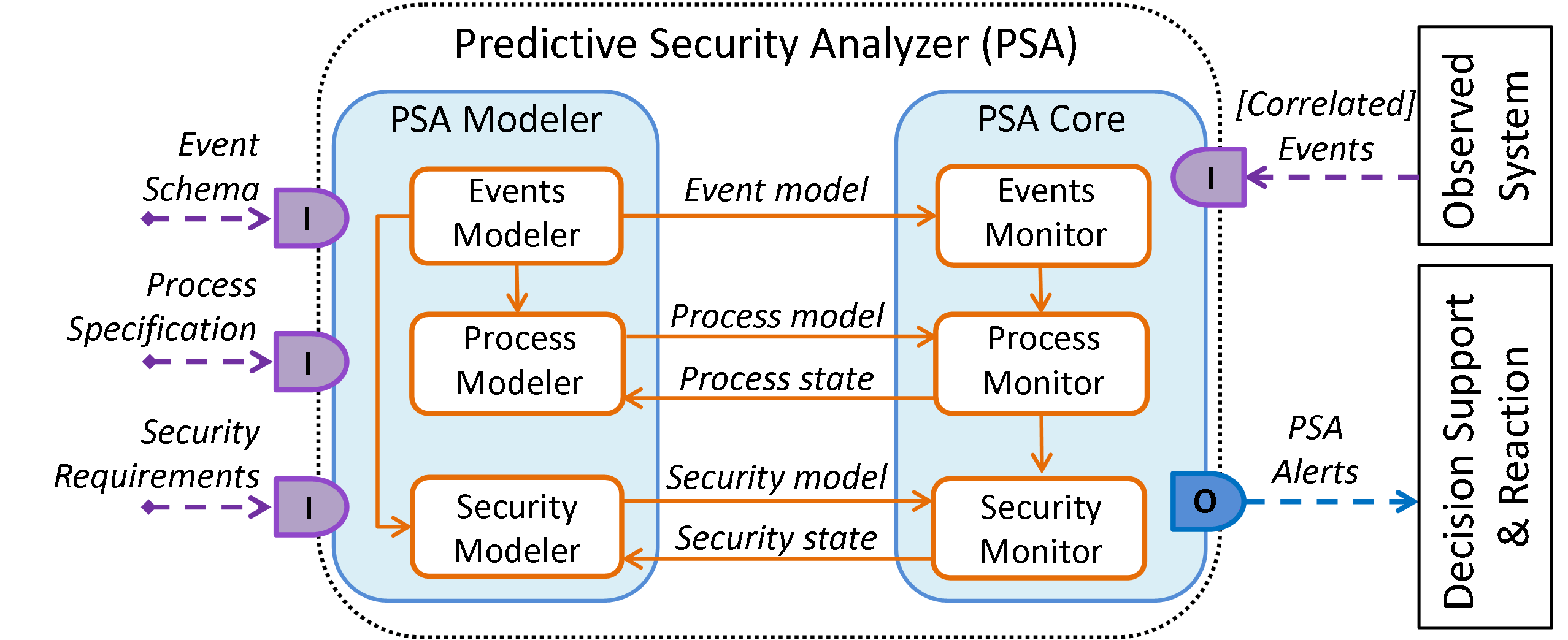
Security management requires model-based methods not only during the development of secure systems (Security by Design). The Predictive Security Analyzer (PSA) shows that models can be used at runtime to detect security-critical situations at an early stage and to assess the associated risk.
Operation
The Predictive Security Analyser utilizes models of the observed system during
runtime for the following purposes:
- Anomaly detection with respect to
behavior anomalies which indicate possible attacks,
-
compliance control with
respect to explicit violations to security policies, and,
-
prediction of critical
situations with respect to safety or security in the near future.
The PSA observes the operation of a system or a Systems of Systems
by analyzing events received from this system. The PSA is not executed
by this observed system but rather by an observing and reacting system.
The PSA takes as an input:
If a critical state or a process anomaly is detected, the PSA
generates an alert that is disseminated for further processing.
Applications
The PSA prototype has been applied in the following scenarios:
The PSA and its integration in a tool chain has been evaluated by four industrial partners
in the project MASSIF.
Partnering
Please contact me if you are interested in the PSA to discuss possibilities for
-
improving security in your specific context, or
-
cooperation in the development of a fully-fledged product
on the basis of the existing prototype.
|
"Security@Runtime" ergänzt "Security by Design"
Zur Verbesserung der Sicherheitseigenschaften in der Entwurfsphase
und bei der Implementierung von Systemen
wurden modellbasierte Methoden in den letzten Jahren stark erforscht
('Security-by-Design'-Prinzip).
Bei der Sicherheitsüberwachung zur Laufzeit
werden diese Methoden aber derzeit nicht genutzt.
Die prädiktive Sicherheitsanalyse bildet eine neuartige Ergänzung
und ein Bindeglied zwischen den etablierten Methoden
Data Mining, Machine Learning, Predictive Analytics, Complex Event Processing und Process Mining.
Das Hauptmerkmal des Ansatzes ist dabei, dass ebenenübergreifende
Prozessmodelle genutzt werden, um die Sicherheit eines komplexen verteilten Systems zur Laufzeit
vorausschauend zu bewerten und damit eine der Situation angepasste proaktive Reaktion zu ermöglichen.
Der Predictive Security Analyser (PSA) implementiert die
Methode der prädiktiven Sicherheitsanalyse.
Damit können Modelle auch während der Laufzeit genutzt werden,
um sicherheitskritische Situationen frühzeitig zu erkennen und
das damit verbundene Risiko zu bewerten.
Funktionsweise
Der PSA nutzt ein ereignisbasiertes Prozessmodell zur Simulation des Prozessverhaltens in der nahen Zukunft und ermöglicht so eine vorausschauende Warnung vor möglichen Gefahren.
Ein neu entwickeltes "Uncertainty Management" ermöglicht eine sofortige semi-automatische Anpassung des Prozessmodells, falls auftretende Abweichungen durch die nat�rliche Evolution der Prozesse ausgelt wurden.
Falls die Abweichungen jedoch von Fehlverhalten oder Stungen des Prozesses ausgelt werden, wird ein Alarm ausgegeben, der auch Entscheidungs- und Reaktionshilfe bietet. Je nach Situation können auch
Trigger für automatische Gegenmassnahmen ausgelöst werden.
Dazu überwacht die PSA-Core Komponente einen komplexen Ereignisstrom, welcher von Prozessen
während der Laufzeit erzeugt wird, mit den folgenden drei Zielen:
-
Anomalieerkennung in Bezug auf Verhaltensanomalien, welche auf mögliche Angriffe hindeuten,
-
Compliance Kontrolle in Bezug auf explizite Verstösse gegen Sicherheitsregeln und
-
Prädiktion von Sicherheitsproblemen in der nahen Zukunft.
Die Kernidee ist dabei, dass in Ergänzung zu existierenden Verfahren,
die statistische Werte aus historischen Messungen verwenden, um Anomalien
zu entdecken, hier das Wissen um den geplanten Kontrollfluss der Prozesse und die dazugehörigen
Sicherheitsanforderungen verwendet wird.
Im Unterschied zu Business Process Monitoring (BPM) bzw. Business Activity Monitoring (BAM),
welches normalerweise
direkt vom BPM-System durchgeführt wird, nutzt der PSA auch (korrelierte) Ereignisse aus
allen direkt oder indirekt beteiligten Systemen auf verschiedenen logischen Ebenen
(wie z.B. SIEM auf der Netzinfrastrukturebene) und kann damit auch Querbezüge
auswerten.
Nutzen
Die prädiktive Sicherheitsanalyse bringt Security- und Compliance-Dimensionen in
traditionelle Prozessanalyse-Prozeduren.
Dies unterstützt die Prozessverantwortlichen bei der Verbesserung der
Sicherheit durch eine kontinuierliche Laufzeitbewertung von kritischen Prozessen mit Hilfe
aller verfügbarer Informationsquellen.
Mittels eines im PSA hinterlegten Modells des vorgeschriebenen Prozessverhaltens
und den dazu passenden Compliance Regeln kann der Prozessverantwortliche:
-
das Erreichen der Prozessziele besser beurteilen,
-
Abweichungen vom geplanten (vorgeschriebenen) Verhalten feststellen und vorhersagen,
-
den laufenden Prozess bzgl. der Sicherheitsrichtlinien überwachen und auditieren,
-
die Behandlung von Störungen besser einschätzen,
-
Schwachstellen im Prozessablauf erkennen und
damit Korrekturen im Prozessablauf besser planen.
Der PSA unterstützt damit ein intelligentes Lifecycle-Sicherheitsmanagement
über den gesamten Wertschöpfungszyklus.
PSA-Technologie unterstützt einen Auditor:
-
durch Protokollierung von Abweichungen vom geplanten Prozessverhalten,
-
bei der Bereitstellung von Änderungsempfehlungen basierend auf der Analyse von erkannten Abweichungen vom beschriebenen Verhalten,
-
bei der quantitativen Bewertung der Compliance bezüglich der Sicherheitsanforderungen durch Protokollierung von geeigneten Messgrössen zur Ermittlung von Kennzahlen.
Belastbare Daten zur Unterstützung der Handlungsempfehlungen werden damit bereitgestellt.
Exemplarische Einsatzbereiche im Internet der Dinge und Dienste
Der Prototyp des PSA wurde bereits in folgenden industriellen Szenarien erprobt:
- Logistik und Industrie 4.0
- Im BMBF Projekt
ADiWa
wurden Authentizitätsanforderungen bzgl. der GPS-Positionen von Fahrzeugen für die
Fracht-Logistik mittels PSA analysiert. Anomalien sind hier z.B. Dinge (RFID) in unerwarteten Positionen (GPS).
- Cyber-physische Systeme und kritische Infrastrukturen
- Die Prozessüberwachung in kritischen Infrastrukturen mittels PSA wurde von einem KMU,
das Steuerungskomponenten für Staudämme entwickelt, erprobt.
- Infrastruktur und Dienste für Kommunikation (Medien), Gesundheit und Kultur
- Die Erkennung komplexer Angriffe mit PSA hat ein Industriepartner im Projekt MASSIF
am
IT-Management der Olympischen Spiele
getestet.
- Finanzen
- Die
Missbrauchserkennung in Finanzdiensten wurde a) von einem
Telekommunikationsunternehmen
mit Realdaten eines mobilen Geldtransferdienstes getestet,
und b) im BMBF Projekt
ACCEPT mit synthetischen Daten zur Anomalieerkennung erforscht.
- IT Outsourcing und Managed Services
- Von einem MASSIF Industriepartner wurden mittels PSA Unregelmässigkeiten im Betrieb eines IT Outsourcing Service untersucht.
Für den Betrieb des PSA zur Laufzeit ist kein Expertenwissen erforderlich.
Die benötigten ausführbaren Modelle können mittels der PSA-Modeller Komponente
aus bereits vorhandenen Prozessspezifikationen erzeugt werden.
Dabei können Spezifikationen in Form von
Ereignisgesteuerten Prozessketten (EPK), Business Process Model Notation (BPMN)
oder Petri Netzen benutzt werden.
Die EPK Notation ist vor allem im deutschsprachigen Raum etabliert und
wird durch Werkzeuge namhafter Hersteller, wie z.B. Software AG (ARIS) und SAP (R/3),
unterstützt.
Falls kein entsprechendes Prozessmodell
vorliegt, kann dieses auch durch Prozess-Mining-Werkzeuge
bereitgestellt werden.
Partner
Bitte sprechen sie uns an, wenn sie sich für den PSA interessieren, die
Einsatzmöglichkeiten zur Verbesserung der Sicherheit in ihrem konkreten Kontext besprechen möchten oder sich an der Entwicklung eines vollwertiges Produktes
auf Basis des vorhandenen Prototypen beteiligen möchten.
|
Publications on Predictive Analysis
Roland Rieke, Maria Zhdanova, and Jürgen Repp (2015),
Security Compliance Tracking of Processes in Networked Cooperating Systems,
Journal of Wireless Mobile Networks, Ubiquitous Computing,
and Dependable Applications (JoWUA), Vol. 6, No. 2, 2015
[Abstract]
[BibTeX]
[Paper (free access)]
|
| Abstract:
Systems of systems that collaborate for a common purpose are called
cooperating systems. Typical examples of novel cooperating systems
are electronic health systems and electronic money transfer systems
but also critical infrastructures, such as future vehicular ad hoc
networks and distributed air traffic management systems. Business
processes and technical workflows control the cooperation of
the networked systems. Important safety and security goals of the
applications, business goals, and external compliance requirements
create security obligations for such processes. These processes
must not only be secure, they must be demonstrably so. To support
this, we present an approach for security compliance tracking of
processes in networked cooperating systems using an advanced method
of predictive security analysis at runtime. At that, operational
models are utilized for: (a) tracking conformance of process
behavior with respect to the specification, (b) detection of
behavior anomalies which indicate possible attacks, (c) tracking
compliance of process behavior with respect to safety and security
requirements, and (d) prediction of possible violations of safety
and security policies in the near future. We provide an extensive
background analysis, introduce the model-based conformance
tracking and uncertainty management algorithm, and describe
security compliance tracking and model-based behavior prediction.
We demonstrate the implementation of the proposed approach on a
critical infrastructure scenario from a European research project.
|
BibTeX:
@ARTICLE{jowua15-6-2-02,
Author = {Roland Rieke and Maria Zhdanova and J\"urgen Repp},
title = {Security Compliance Tracking of Processes in Networked Cooperating Systems},
journal = {Journal of Wireless Mobile Networks, Ubiquitous Computing, and Dependable Applications (JoWUA)},
volume = {6},
number = {2},
year = {2015},
month = {June},
pages = {21--40},
ee = {http://isyou.info/jowua/papers/jowua-v6n2-2.pdf}
}
|
Roland Rieke (2014),
Security Analysis of System Behaviour - From 'Security by Design' to 'Security at Runtime' -,
PhD thesis at Philipps-Universität Marburg
[Abstract]
[BibTeX]
[Überblick]
[Info]
[Dissertation (free access, 11 MB)]
|
| Abstract:
The Internet today provides the environment for novel applications and
processes which may evolve way beyond pre-planned scope and
purpose. Security analysis is growing in complexity with the increase
in functionality, connectivity, and dynamics of current electronic
business processes. Technical processes within critical
infrastructures also have to cope with these developments. To tackle
the complexity of the security analysis, the application of models is
becoming standard practice. However, model-based support for security
analysis is not only needed in pre-operational phases but also during
process execution, in order to provide situational security awareness
at runtime.
This cumulative thesis provides three major contributions to modelling
methodology.
Firstly, this thesis provides an approach for model-based analysis and
verification of security and safety properties in order to support
fault prevention and fault removal in system design or redesign.
Furthermore, some construction principles for the design of
well-behaved scalable systems are given.
The second topic is the analysis of the exposition of vulnerabilities
in the software components of networked systems to exploitation by
internal or external threats. This kind of fault forecasting allows
the security assessment of alternative system configurations and
security policies. Validation and deployment of security policies
that minimise the attack surface can now improve fault tolerance and
mitigate the impact of successful attacks.
Thirdly, the approach is extended to runtime applicability. An
observing system monitors an event stream from the observed system
with the aim to detect faults - deviations from the specified
behaviour or security compliance violations - at runtime.
Furthermore, knowledge about the expected behaviour given by an
operational model is used to predict faults in the near
future. Building on this, a holistic security management strategy is
proposed. The architecture of the observing system is described and
the applicability of model-based security analysis at runtime is
demonstrated utilising processes from several industrial scenarios.
The results of this cumulative thesis are provided by 19 selected
peer-reviewed papers.
|
BibTeX:
@PHDTHESIS{drr2014,
author = {Roland Rieke},
title = {{Security Analysis of System Behaviour - From 'Security by Design' to 'Security at Runtime' -}},
url = {http://archiv.ub.uni-marburg.de/diss/z2014/0499},
school = {Philipps-Universit\"at Marburg, Germany},
year = {2014},
month={Dec}
}
|
Maria Zhdanova, Jürgen Repp, Roland Rieke, Chrystel Gaber, and Baptiste Hemery (2014),
No Smurfs: Revealing Fraud Chains in Mobile Money Transfers,
ARES 2014 (Best Paper Session)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract: Mobile Money Transfer (MMT) services provided
by mobile network operators enable funds transfers made on mobile
devices of end-users, using digital equivalent of cash (electronic
money) without any bank accounts involved. MMT simplifies banking
relationships and facilitates financial inclusion, and, therefore,
is rapidly expanding all around the world, especially in
developing countries. MMT systems are subject to the same controls
as those required for financial institutions, including the
detection of Money Laundering (ML) a source of concern for MMT
service providers. In this paper we focus on an often practiced ML
technique known as micro-structuring of funds or smurfing and
introduce a new method for detection of fraud chains in MMT
systems. Whereas classical detection methods are based on machine
learning and data mining, this work builds on Predictive Security
Analysis at Runtime (PSA@R), a model-based approach for
event-driven process analysis. We provide an extension to PSA@R
which allows us to identify fraudsters in an MMT service
monitoring network behavior of its end-users. We evaluate our
method on simulated transaction logs, containing approximately
460,000 transactions for 10,000 end-users, and compare it with
classical fraud detection approaches. With 99.81% precision and
90.18% recall, we achieve better recognition performance in
comparison with the state of the art.
|
BibTeX:
@incollection{ares2014,
author={Maria Zhdanova and J\"urgen Repp and Roland Rieke and Chrystel Gaber and Baptiste Hemery},
title={No Smurfs: Revealing Fraud Chains in Mobile Money Transfers},
year={2014},
booktitle={Proceedings of 2014 International Conference on Availability, Reliability and Security, ARES 2014},
pages={11-20},
isbn={978-1-4799-4223-7/14},
doi={10.1109/ARES.2014.10},
publisher = {IEEE Computer Society},
}
|
Roland Rieke, Maria Zhdanova, Jürgen Repp, Romain Giot, and Chrystel Gaber (2014),
Verhaltensanalyse zur Erkennung von Missbrauch mobiler Geldtransferdienste,
GI Sicherheit 2014, Lecture Notes in Informatics P-228
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
|
| Abstract:
Die fortlaufende Überwachung von Transaktionen auf Geldwäscheverdacht
ist Finanzinstituten in Deutschland und anderen Ländern vorgeschrieben.
Smurfing ist eine Form der Geldwäsche, bei der durch den Transfer
vieler kleiner Geldbeträge auf unterschiedlichen Wegen mit der Hilfe von
Strohmännern ein hoher Geldbetrag unauffällig transferiert werden soll.
In dieser Arbeit betrachten wir das Smurfing-Risiko im Rahmen
mobiler Geldtransferdienste.
Insbesondere beschreiben wir eine Methode zur vorbeugenden Sicherheitsanalyse zur Laufzeit,
welche das Prozessverhalten in einem Geldtransfer-Service in Bezug auf Transaktionen beobachtet
und versucht, es mit dem erwarteten Verhalten zu vergleichen, welches durch ein Prozessmodell
vorgegeben ist.
Wir analysieren Abweichungen von der vorgegebenen Verhaltensspezifikation auf Anomalien,
die einen möglichen Missbrauch des Finanzdienstes durch Geldwäscheaktivitäten anzeigen.
Wir bewerten die Anwendbarkeit der Vorgehensweise und
beschreiben Messungen der Rechen- und Erkennungsleistung eines prototypischen Werkzeugs
basierend auf realen und simulierten Betriebsprotokollen.
Das Ziel der Experimente ist es, basierend auf Eigenschaften des realen
Finanzdienstes, Missbrauchsmuster in synthetisiertem Prozessverhalten
mit eingefügten Geldwäscheaktivitäten zu erkennen.
|
BibTeX:
@inproceedings{gi2014,
author={Roland Rieke and Maria Zhdanova and J\"urgen Repp and Romain Giot and Chrystel Gaber},
editor= {Stefan Katzenbeisser and Volkmar Lotz and Edgar Weippl},
location={Wien},
booktitle = {GI Sicherheit 2014},
title={{Verhaltensanalyse zur Erkennung von Missbrauch mobiler Geldtransferdienste}},
month={March},
year={2014},
series = {Lecture Notes in Informatics (LNI) -- Proceedings},
isbn= {978-3-88579-622-0},
volume={P-228},
pages={271-282},
url = {http://subs.emis.de/LNI/Proceedings/Proceedings228/article31.html},
publisher={GI}
}
|
Roland Rieke, Jürgen Repp, Maria Zhdanova, and Jörn Eichler (2014),
Monitoring Security Compliance of Critical Processes,
The 22th Euromicro International Conference on Parallel, Distributed and Network-Based Computing (PDP 2014)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Enforcing security in process-aware information systems
at runtime requires the monitoring of systems'
operation using process information. Analysis of this information with
respect to security and compliance aspects is growing in complexity
with the increase in functionality, connectivity, and dynamics of
process evolution.
To tackle this complexity, the application of models is becoming standard
practice. Considering today's frequent changes to processes,
model-based support for security and compliance analysis is not
only needed in pre-operational phases but also at runtime.
This paper presents an approach to support evaluation of
the security status of processes at runtime.
The approach is based on operational formal models derived from
process specifications and security policies comprising technical,
organizational, regulatory and cross-layer aspects.
A process behavior model is synchronized by events from the running process and
utilizes prediction of expected close-future states to find possible
security violations and allow early decisions on countermeasures.
The applicability of the approach is exemplified by a misuse case scenario from a
hydroelectric power plant.
|
BibTeX:
@INPROCEEDINGS{pdp2014,
author={Rieke, Roland and Repp, J\"urgen and Zhdanova, Maria and Eichler, J\"orn},
booktitle={Parallel, Distributed and Network-Based Processing (PDP), 2014 22nd Euromicro International Conference on},
title={Monitoring Security Compliance of Critical Processes},
year={2014},
month={Feb},
pages={552-560},
keywords={critical infrastructures;predictive security analysis;process behavior analysis;security information and event management;security modeling and simulation;security monitoring},
doi={10.1109/PDP.2014.106},
ISSN={1066-6192},
url = {http://ieeexplore.ieee.org/xpl/articleDetails.jsp?arnumber=6787328},
publisher = {IEEE Computer Society},
}
|
Roland Rieke, Maria Zhdanova, Jürgen Repp, Romain Giot, and Chrystel Gaber (2013),
Fraud Detection in Mobile Payment Utilizing Process Behavior Analysis,
RaSIEM 2013 at ARES 2013
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Generally, fraud risk implies any intentional deception made for
financial gain. In this paper, we consider this risk in the field of
services which support transactions with electronic money.
Specifically, we apply a tool for predictive security analysis at runtime
which observes process behavior with respect to transactions
within a money transfer service and tries to match it with expected behavior
given by a process model. We analyze deviations from the given
behavior specification for anomalies that indicate a possible misuse
of the service related to money laundering activities.
We evaluate the applicability of the
proposed approach and
provide measurements on computational and recognition performance of
the tool - Predictive Security Analyser (PSA) - produced using real operational and simulated logs.
The goal of the experiments is to detect misuse patterns reflecting a given money
laundering scheme in synthetic process behavior based on properties
captured from real world transaction events.
|
BibTeX:
@incollection{rasiem2013,
author={Roland Rieke and Maria Zhdanova and J\"urgen Repp and Romain Giot and Chrystel Gaber},
title={Fraud Detection in Mobile Payment Utilizing Process Behavior Analysis},
year={2013},
booktitle={Proceedings of 2013 International Conference on Availability, Reliability and Security, ARES 2013},
pages={662-669},
isbn={978-0-7695-5008-4},
doi={10.1109/ARES.2013.87},
publisher = {IEEE Computer Society},
}
|
Roland Rieke, Luigi Coppolino, Andrew Hutchison, Elsa Prieto, and Chrystel Gaber (2012),
Security and Reliability Requirements for Advanced Security Event Management,
MMM-ACNS 2012, (Springer LNCS 7531)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
This paper addresses security information management in complex application scenarios. Security Information and Event Management (SIEM) systems collect and examine security related events, with the goal of providing a unified view of the monitored systems' security status. While various SIEMs are in production, there is scope to extend the capability and resilience of these systems. The use of SIEM technology in four disparate scenario areas is used in this paper as a catalyst for the development and articulation of Security and Reliability requirements for advanced security event management. The scenarios relate to infrastructure management for a large real-time sporting event, a mobile money payment system, a managed services environment and a cyber-physical dam control system. The diversity of the scenarios enables elaboration of a comprehensive set of Security and Reliability requirements which can be used in the development of future SIEM systems.
|
BibTeX:
@incollection{mmm-acnsb:2012,
year={2012},
isbn={978-3-642-33703-1},
booktitle={Computer Network Security},
volume={7531},
series={Lecture Notes in Computer Science},
editor={Kotenko, Igor and Skormin, Victor},
doi={10.1007/978-3-642-33704-8_15},
title={Security and Reliability Requirements for Advanced Security Event Management},
url={http://dx.doi.org/10.1007/978-3-642-33704-8_15},
publisher={Springer Berlin Heidelberg},
keywords={security requirements; security information and event management; SIEM; architecting trustworthy systems},
author={Rieke, Roland and Coppolino, Luigi and Hutchison, Andrew and Prieto, Elsa and Gaber, Chrystel},
pages={171-180}
}
|
Roland Rieke, Elsa Prieto, Rodrigo Diaz, Herve Debar, and Andrew Hutchison (2012),
Challenges for Advanced Security Monitoring - The MASSIF
project,
TrustBus 2012, (Springer LNCS 7449)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
The vision of creating a next-generation Security Information and
Event Management environment drives the development of an
architecture which provides for trustworthy and resilient
collection of security events from source systems, processes and applications.
A number of novel inspection and analysis techniques are applied to
the events collected to provide high-level situational
security awareness, not only on the network level but also at the
service level where high-level threats such as money laundering
appear. An anticipatory impact analysis will predict the
outcome of threats and mitigation strategies and thus enable
proactive and dynamic response.
|
BibTeX:
@incollection {trustbus:2012,
author = {Rieke, Roland and Prieto, Elsa and Diaz, Rodrigo and Debar, Herv{\'e} and Hutchison, Andrew},
affiliation = {Fraunhofer Institute SIT, Darmstadt, Germany},
title = {Challenges for Advanced Security Monitoring -- The MASSIF Project},
booktitle = {Trust, Privacy and Security in Digital Business},
series = {Lecture Notes in Computer Science},
editor = {Fischer-H\"ubner, Simone and Katsikas, Sokratis and Quirchmayr, Gerald},
publisher = {Springer Berlin / Heidelberg},
isbn = {978-3-642-32286-0},
keyword = {Computer Science},
pages = {222-223},
volume = {7449},
url = {http://dx.doi.org/10.1007/978-3-642-32287-7_23},
doi = {10.1007/978-3-642-32287-7_23},
year = {2012}
}
|
Elsa Prieto, Rodrigo Diaz, Luigi Romano, Roland Rieke, and Mohammed Achemlal (2012),
MASSIF: A Promising Solution to Enhance Olympic Games IT Security,
Global Security, Safety and Sustainability & e-Democracy, (Springer LNICST 99)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
|
| Abstract:
Nowadays, Olympic Games have become one of the most profitable
global media events, becoming at the same way more and more attractive target
from the terrorist perspective due to their media diffusion and international
dimension. Critical for the success of such a highly visible event is protecting
and securing the business and the supporting cyber-infrastructure enabling it. In
this context, the MASSIF project aims to provide a new generation SIEM
framework for service infrastructures supporting intelligent, scalable, and
multi-level/multi-domain security event processing and predictive security
monitoring.
|
BibTeX:
@incollection {pdrra:2012,
author = {Prieto, Elsa and Diaz, Rodrigo and Romano, Luigi and Rieke, Roland and Achemlal, Mohammed},
affiliation = {Atos Research and Innovation (ARI), Atos Origin, Europe},
title = {MASSIF: A Promising Solution to Enhance Olympic Games IT Security},
booktitle = {Global Security, Safety and Sustainability \& e-Democracy},
series = {Lecture Notes of the Institute for Computer Sciences, Social Informatics and Telecommunications Engineering},
editor = {Georgiadis, Christos K. and others},
publisher = {Springer Berlin Heidelberg},
isbn = {978-3-642-33447-4},
keyword = {Computer Science},
pages = {139-147},
volume = {99},
url = {http://dx.doi.org/10.1007/978-3-642-33448-1_20},
doi = {10.1007/978-3-642-33448-1_20},
year = {2012}
}
|
Paulo Verissimo, Nuno Neves, Alexander Goller, Alberto Roman Limancero, Susana González, Rubén Torres, Luigi Romano, Salvatore D'Antonio, Herv� Debar, Roland Rieke, Zaharina Stoynova, Igor Kotenko, Andrey Chechulin, Ricardo Jimenez-Peris, Claudio Soriente, Nizar Kheir, and Jouni Viinikka (2012),
MASSIF Architecture Document,
FP7-257475 MASSIF European project
[BibTeX]
[MASSIF Architecture document]
|
BibTeX:
@techreport{other-MASSIF-arch,
author={Paulo Verissimo and Nuno Neves and Alexander Goller and Alberto Roman
Limancero and Susana González and Rubén Torres and Luigi Romano and Salvatore D'Antonio and Herv� Debar and Roland Rieke and Zaharina Stoynova and Igor Kotenko and Andrey Chechulin and Ricardo Jimenez-Peris and Claudio
Soriente and Nizar Kheir and Jouni Viinikka},
title={MASSIF Architecture Document},
institution={FP7-257475 MASSIF European project},
organization={FP7-257475 MASSIF European project},
year={2012},
month={April},
url = {http://rieke.link/MASSIF_Architecture_document.pdf}
}
|
Jörn Eichler and Roland Rieke (2011),
Model-based Situational Security Analysis,
6th International Workshop on [email protected] in conjunction with MODELS 2011.
[Abstract]
[BibTeX]
[Paper (free access)]
[Author's version]
[Slides]
|
| Abstract: Security analysis is growing in complexity with the increase in functionality, connectivity, and dynamics of current electronic business processes. To tackle this complexity, the application of models in pre-operational phases is becoming standard practice. But also runtime models are increasingly applied to analyze and validate the actual security status of business process instances. In this paper we present an approach to support not only model-based evaluation of the current security status of business process instances but also to allow for decision support by analyzing close-future process states. Our approach is based on operational formal models derived from development-time process and security models. This paper exemplifies our approach utilizing real world processes from the logistics domain and demonstrates the systematic development and application of runtime models for situational security analysis.
|
BibTeX:
@incollection{eichler:rieke:2011,
author = {J\"orn Eichler and Roland Rieke},
title = {{Model-based Situational Security Analysis}},
booktitle = {Proceedings of the 6th International Workshop on [email protected] at the ACM/IEEE 14th International Conference on Model Driven Engineering Languages and Systems (MODELS 2011), Wellington, New Zealand},
pages = {25-36},
volume = 794,
editors = {Nelly Bencomo, Gordon Blair, Betty Cheng, Robert France, Cédric Jeanneret},
publisher = {Nelly Bencomo, Gordon Blair, Betty Cheng, Robert France, Cédric Jeanneret},
series = {CEUR Workshop Proceedings},
url = {http://ceur-ws.org/Vol-794/paper_1.pdf},
issn={1613-0073},
year = {2011}
}
|
Roland Rieke and Zaharina Stoynova (2010),
Predictive Security Analysis for Event-Driven Processes,
MMM-ACNS-2010, (Springer LNCS 6258)
[Abstract]
[BibTeX]
[Paper]
[Author's version]
[Slides]
|
| Abstract: This paper presents an approach for predictive security analysis in a business process execution environment. It is based on operational formal models and leverages process and threat analysis and simulation techniques in order to be able to dynamically relate events from different processes and architectural layers and evaluate them with respect to security requirements. Based on this, we present a blueprint of an architecture which can provide decision support by performing dynamic simulation and analysis while considering real-time process changes. It allows for the identification of close-future security-threatening process states and will output a predictive alert for the corresponding violation. |
BibTeX:
@incollection{Rieke:Stoynova:2010,
author = {Rieke, Roland and Stoynova, Zaharina},
affiliation = {Fraunhofer Institute for Secure Information Technology SIT, Darmstadt, Germany},
title = {Predictive Security Analysis for Event-Driven Processes},
booktitle = {Computer Network Security},
series = {Lecture Notes in Computer Science},
editor = {Kotenko, Igor and Skormin, Victor},
publisher = {Springer Berlin / Heidelberg},
isbn = {978-3-642-14705-0},
keyword = {Computer Science},
pages = {321-328},
volume = {6258},
url = {http://dx.doi.org/10.1007/978-3-642-14706-7_25},
doi = {10.1007/978-3-642-14706-7_25},
year = {2010}
}
|
|

