RulEth: Genetic Programming-Driven Derivation of Security Rules for Automotive Ethernet (ECML PKDD 2023 best paper award for the Applied Data Science track)
A Context-Aware on-board Intrusion Detection System (Under review; Preprint available)
Evaluation of Decision Tree-Based Rule Derivation for Intrusion Detection in Automotive Ethernet (ITCCN-2023/TrustCom-2023)
A Policy-driven Architecture for Security Incident Mitigation in Connected Vehicles (SCIS 2023)
Collaborative Security Patterns for Automotive Electrical/Electronic Architectures (Springer 2023)
CAHOOT: A Context-Aware veHicular intrusiOn detectiOn sysTem (MLTrustCom 2022)
Datenverarbeitung und Cybersicherheit in der Fahrzeugautomatisierung - Rechtliche und technische Anforderungen im Verbund (MultiMedia und Recht 2022)
Decision Tree-Based Rule Derivation for Intrusion Detection in Safety-Critical Automotive Systems (PDP 2022)
SECPAT: Security Patterns for Resilient Automotive E/E Architectures (PDP 2022)
ThreatSurf: A method for automated Threat Surface assessment in automotive cybersecurity engineering (MICPRO 2022)
Cyberattack detection in vehicles using characteristic functions, artificial neural networks and visual analysis (SPIIRAS 2021)
In-vehicle detection of targeted CAN bus attacks (ARES 2021)
Attack Surface Assessment for Cybersecurity Engineering in the Automotive Domain (PDP 2021)
Continuous Fields: Enhanced In-Vehicle Anomaly Detection using Machine Learning Models (SIMPAT 2020)
SEPAD - Security Evaluation Platform for Autonomous Driving (PDP 2020)
ECU-Secure: Characteristic Functions for In-Vehicle Intrusion Detection (IDC 2019)
|
The connection of automotive systems with other systems such as road-side units, other vehicles, and various servers in the Internet opens up new ways for attackers to remotely access safety relevant subsystems within a connected car. This safety critical technology presents major challenges in the secure design of the involved systems and protocols. Security of vehicular ecosystems is thus of utmost importance for the general acceptance of such systems. Ongoing insights into new threats are constantly revealing new vulnerabilities and it is very likely that attackers will attempt to exploit them. It is thus very important to improve security of in-vehicle networks and as long as there are no effective means to prevent specific attacks, there should be methods in place to automatically detect them and react to the alerts. 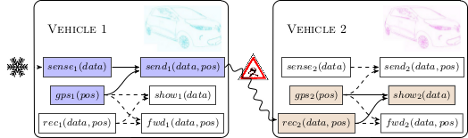 The security requirements elicitation step in the security engineering process for automotive systems and ecosystems not only provides input to the secure on-board architecture design but also contributes to security compliance verification for testing and runtime monitoring. In the project EVITA we participated in the development of a method which is described in detail in EVITA deliverable D2.3 [D2.3]. This method is referenced in the SAE J3061 Cybersecurity Guidebook for Cyber-Physical Vehicle Systems, an important document on recommended practice for the automotive industry. In new work, we provide an attack surface assessment for cybersecurity engineering in the automotive domain, compliant to ISO/SAE 21434 [PDP2021]. |
To enable researchers to develop, implement, and evaluate new security solutions for autonomous vehicles, we propose a new security evaluation platform called SEPAD and a dedicated development process for testing security mechanisms with it [PDP2020]. Machine learning methods such as OCSVM, SVM, Neural Networks, LSTM or Process Mining can be applied to in-vehicle event-streams such as CAN-bus in order to learn "normal" behavior of specific vehicles. Deviations from normal behavior can be utilized for in-vehicle intrusion detection at edge components. Machine learning methods featuring message frequency, payload consistency, and contextual fitting can be applied for adaption of attack classifiers and selection of an appropriate response. Conformance tracking is the capability to detect deviations of observed events from expected events in the current state. 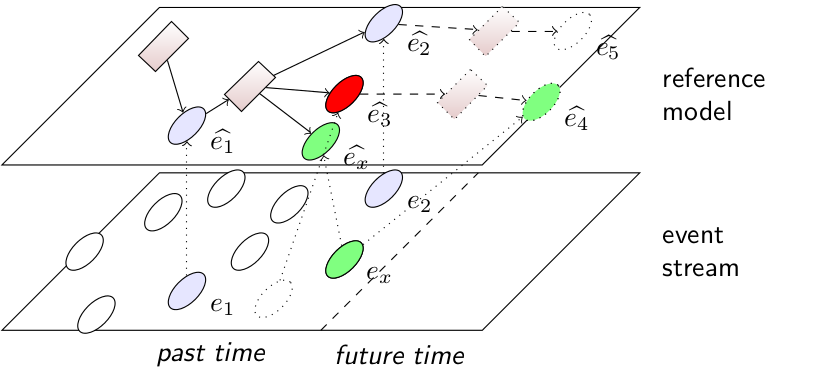 We analyze the behavior of an automotive system based on monitored messages of electronic control units. The aim is to compare the measured behavior of the system with a model that reflects the expected behavior and to reason about possible attack attempts. |
|
Marco De Vincenzi, Gianpiero Costantino, Ilaria Matteucci, Florian Fenzl, Christian Plappert, Roland Rieke, Daniel Zelle A Systematic Review on Security Attacks and Countermeasures in Automotive Ethernet, Accepted for publication in ACM Computing Surveys 2023 |
| Abstract: In the last years, the automotive industry has experienced a technological revolution driven by the increasing demand of connectivity and data to develop driver-assistance systems, autonomous vehicles, and improve the mobility experience. To provide higher bandwidth in in-vehicle communication networks (IVNs), carmakers are choosing Ethernet technology, which becomes Automotive Ethernet when applied in IVNs. However, with the rise of vehicle connectivity, the cybersecurity of vehicle systems has become a primary concern for the automotive industry. To address this issue, we conducted a systematic review, deeply analyzing the impact of Automotive Ethernet on security, safety, and comparing it with the current in-vehicle communication solutions like CAN protocol. We retrieved the key security attacks and mitigations proposed in the current literature to highlight their significance, including a mapping between the regulation UNECE WP.29 R155 and the retrieved answers. We found that the industry has only implemented some automotive-dedicated Ethernet solutions to date. In the near future, the vehicle and road ecosystems may require more exclusive automotive solutions to meet specific constraints such as low latency. Our results can provide a comprehensive baseline, both for industry and academia, for the current and future development of Automotive Ethernet. |
BibTeX:
@article{deVincenzi2023,
author = {De Vincenzi, Marco and Costantino, Gianpiero and Matteucci, Ilaria and Fenzl, Florian and Plappert, Christian and Rieke, Roland and Zelle, Daniel},
title = {A Systematic Review on Security Attacks and Countermeasures in Automotive Ethernet},
year = {2023},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
issn = {0360-0300},
url = {https://doi.org/10.1145/3637059},
doi = {10.1145/3637059},
abstract = {In the last years, the automotive industry has experienced a technological revolution driven by the increasing demand of connectivity and data to develop driver-assistance systems, autonomous vehicles, and improve the mobility experience. To provide higher bandwidth in in-vehicle communication networks (IVNs), carmakers are choosing Ethernet technology, which becomes Automotive Ethernet when applied in IVNs. However, with the rise of vehicle connectivity, the cybersecurity of vehicle systems has become a primary concern for the automotive industry. To address this issue, we conducted a systematic review, deeply analyzing the impact of Automotive Ethernet on security, safety, and comparing it with the current in-vehicle communication solutions like CAN protocol. We retrieved the key security attacks and mitigations proposed in the current literature to highlight their significance, including a mapping between the regulation UNECE WP.29 R155 and the retrieved answers. We found that the industry has only implemented some automotive-dedicated Ethernet solutions to date. In the near future, the vehicle and road ecosystems may require more exclusive automotive solutions to meet specific constraints such as low latency. Our results can provide a comprehensive baseline, both for industry and academia, for the current and future development of Automotive Ethernet.},
note = {Just Accepted},
journal = {ACM Comput. Surv.},
month = {dec},
keywords = {UNECE R155, automotive, OSI model, Ethernet, safety, security}
}
|
|
Felix Gail, Roland Rieke, Florian Fenzl, Christoph Krauß Evaluation of Decision Tree-Based Rule Derivation for Intrusion Detection in Automotive Ethernet , The International Symposium on Intelligent and Trustworthy Computing, Communications, and Networking (ITCCN-2023) in conjunction with the 22nd IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom-2023) |
| Abstract: The digitization and networking of safety-critical systems also enables attacks that can have devastating consequences. Thus, appropriate security measures are required. In this work, we investigate a novel approach for security monitoring adapted to the requirements and properties of safety-critical systems. In particular, we evaluate and adapt a decision tree-based detection method that is not only explainable in the sense that the internal processes of the software can be explained to the decision maker, but we use the decision tree and the generated rules to understand exactly which attributes of a message are used for identification of the attack were used. This supports experts in the decision-making process and can also be used for automated countermeasure generation. We demonstrate the detection method on an Automotive Ethernet protocol that is being introduced in modern vehicles to replace or complement currently used bus communication. |
BibTeX:
@INPROCEEDINGS{Gail2023b,
author={Gail, Felix and Rieke, Roland and Fenzl, Florian and Krauß, Christoph},
booktitle={2023 IEEE 22nd International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom)},
title={Evaluation of Decision Tree-Based Rule Derivation for Intrusion Detection in Automotive Ethernet},
year={2023},
volume={},
number={},
pages={1392-1399},
keywords={Privacy;Protocols;Ethernet;Particle measurements;Generators;Security;Decision trees;Security of Connected Vehicles;Intrusion Detection;Automated Rule Generation;Machine Learning;Anomaly Detection;Decision Trees;Automotive Ethernet},
doi={10.1109/TrustCom60117.2023.00190},
ISSN={2324-9013},
month={Nov},}
|
|
Felix Gail, Roland Rieke, Florian Fenzl RulEth: Genetic Programming-Driven Derivation of Security Rules for Automotive Ethernet, Accepted at European Conference on Machine Learning and Principles and Practice of Knowledge Discovery in Databases (ECML PKDD 2023 best paper award for the Applied Data Science track) |
| Abstract: Handcrafted rule-based intrusion detection systems tend to overlook sophisticated intrusions due to unexpected cyberattacker behaviors or human error in analyzing complex control flows. Current machine learning systems, mostly based on artificial neural networks, have the inherent problem that models cannot be verified since the decisions depend on probabilities. To bridge the gap between handcrafted rule systems and probability-based systems, our approach uses genetic programming to generate rules that are verifiable, in the sense that one can confirm that the extracted pattern matches a known attack. The RulEth rules language is designed to be predictive of a packet window, which allows the system to detect anomalies in message flow. Alerts are enriched to include the root cause about the characterization as an anomalous event, which in turn supports decisions to trigger countermeasures. Although the attacks examined in this work are far more complex than those considered in most other works in the automotive domain, our results show that most of the attacks examined can be well identified. By being able to evaluate each rule generated separately, the rules that are not working effectively can be sorted out, which improves the robustness of the system. Furthermore, using design flaws found in a public dataset, we demonstrate the importance of verifiable models for reliable systems. |
BibTeX:
@INPROCEEDINGS{Gail2023,
author = {Felix Gail and Roland Rieke and Florian Fenzl},
editor = {Gianmarco De Francisci Morales and Claudia Perlich and Natali Ruchansky and
Nicolas Kourtellis and Elena Baralis and Francesco Bonchi},
title = {RulEth: Genetic Programming-Driven Derivation of Security Rules for Automotive Ethernet},
booktitle = {Machine Learning and Knowledge Discovery in Databases: Applied Data
Science and Demo Track - European Conference, {ECML} {PKDD} 2023,
Turin, Italy, September 18-22, 2023, Proceedings, Part {VII}},
series = {Lecture Notes in Computer Science},
volume = {14175},
pages = {192--209},
publisher = {Springer},
year = {2023},
url = {https://doi.org/10.1007/978-3-031-43430-3\_12},
doi = {10.1007/978-3-031-43430-3\_12},
month = {September}}
|
|
Davide Micale, Ilaria Matteucci, Florian Fenzl, Roland Rieke, Giuseppe Patan� A Context-Aware on-board Intrusion Detection System, |
| Abstract: Modern vehicles are becoming increasingly attractive from the perspective of possible intruders. The main reasons are twofold: modern vehicles are now connected to the outside world via Wi-Fi, Bluetooth, and mobile connection, such as LTE and 5G, and the increasing complexity of the on-board software enlarges the attack surface. In this article, we introduce CAHOOTv2, a context-sensitive intrusion detection system (IDS) that uses the vehicle~s sensors to determine driver habits and gather information about the environment to detect intruders. We use hyperparameter tuning to increase detection accuracy. To demonstrate the validity of the algorithm, we collected driving data from both an Artificial Intelligence (AI) and 39 humans. We include the AI driver to demonstrate that CAHOOTv2 is able to detect intrusions when the driver is both a human or an AI. The dataset is obtained using a modified version of MetaDrive simulator where we consider also the presence of an intruder able to perform the following types of intrusions: denial of service, replay, spoofing, additive and selective attacks. We make several experiments showing the benefits of hyperparameters tuning. The results of CAHOOTv2 are promising on detection of intrusions. |
BibTeX:
@INPROCEEDINGS{Micale2023,
author={},
booktitle={},
title={},
doi=(https://doi.org/10.21203/rs.3.rs-2650857/v1},
year={2023},
month={}}
|
|
Florian Fenzl, Felix Gail, Lukas Jäger, Christian Plappert, Roland Rieke, Theo Dimitrakos, Ali Hariri, Hussein Joumaa A Policy-driven Architecture for Security Incident Mitigation in Connected Vehicles, SCIS 2023, 2023 Symposium on Cryptography and Information Security, Fukuoka, Japan, Jan. 24-27, 2023 |
| Abstract: With vehicle networks increasing more and more in complexity to enable more advanced features, such as autonomous driving, their cyberattack surface increases. In order to mitigate upcoming cyberattacks, more sophisticated and adaptable security approaches are required. Especially critical is the secure implementation of usage control systems within automotive networks since the increased communication with external entities provides attackers with new ways to infiltrate the vehicle network. Modern standard access management systems have difficulty dynamically adapting to new situations or responding to potential attacks. To improve security and adaptability of usage control systems, we propose means to integrate additional in-vehicle security measurement and verification mechanisms, e.g., based on an Intrusion Detection System or Hardware Trust Anchors like Trusted Platform Modules, with our policy driven usage control system. This allows us to incorporate runtime and boot-time security incidents into our policy decisions. In addition, we discuss the described system using some application scenarios for intrusions as an example. |
BibTeX:
@INPROCEEDINGS{Fenzl2023,
author={Florian Fenzl and Felix Gail and Lukas J\"ager and Christian Plappert and Roland Rieke and Theo Dimitrakos and Ali Hariri and Hussein Joumaa},
booktitle={},
title={A Policy-driven Architecture for Security Incident Mitigation in Connected Vehicles},
year={2023},
month={January}}
|
|
Florian Fenzl, Christian Plappert, Roland Rieke, Daniel Zelle, Gianpiero Costantino, Marco De Vincenzi and Ilaria Matteucci� Collaborative Security Patterns for Automotive Electrical/Electronic Architectures, Collaborative Approaches for Cyber Security in Cyber-Physical Systems, Springer 2023 |
| Abstract: In this chapter, we describe several security design patterns that collaboratively consider various cybersecurity aspects with the aim to ensure compliance with cybersecurity requirements for a certified cybersecurity and software update management system imposed by the recent United Nations regulations. Automated driving requires increasing networking of vehicles, which in turn expands their attack surface. The security design patterns enable the detection of anomalies in the firmware at boot, ensure secure communication in the vehicle and detect anomalies in in-vehicle communications, prevent unauthorized electronic control units from successfully transmitting messages, provide a way to transmit and aggregate security-related events within a vehicle network, and report to entities external to the vehicle. Using the example of a future high-level automotive Electrical/Electronic architecture, we also describe how these security design patterns can be used to become aware of the current attack situation and to react to it. |
BibTeX:
@Inbook{Fenzl2023,
author="Fenzl, Florian
and Plappert, Christian
and Rieke, Roland
and Zelle, Daniel
and Costantino, Gianpiero
and De Vincenzi, Marco
and Matteucci, Ilaria",
editor="Dimitrakos, Theo
and Lopez, Javier
and Martinelli, Fabio",
title="Collaborative Security Patterns for Automotive Electrical/Electronic Architectures",
bookTitle="Collaborative Approaches for Cyber Security in Cyber-Physical Systems",
year="2023",
publisher="Springer International Publishing",
address="Cham",
pages="63--97",
isbn="978-3-031-16088-2",
doi="10.1007/978-3-031-16088-2_4",
url="https://doi.org/10.1007/978-3-031-16088-2_4"
}
|
|
Davide Micale, Gianpiero Costantino, Ilaria Matteucci, Florian Fenzl, Roland Rieke and Giuseppe Patane CAHOOT: A Context-Aware veHicular intrusiOn detectiOn sysTem, The 3rd International Workshop on Machine Learning for Trust, Security and Privacy in Computing and Communications (MLTrustCom 2022) In conjunction with The 21st IEEE International Conference on Trust, Security and Privacy in Computing and Communications (IEEE TrustCom 2022) [Abstract] [Bibtex] [Paper ] <-- [Author created version]--> |
| Abstract: Software in modern vehicles is becoming increasingly complex and subject to vulnerabilities that an intruder can exploit to alter the functionality of vehicles. To this purpose, we introduce CAHOOT, a novel context-aware Intrusion Detection System (IDS) capable of detecting potential intrusions in both human and autonomous driving modes. In CAHOOT, context information consists of data collected at run-time by vehicle's sensors and engine. Such information is used to determine drivers' habits and information related to the environment, like traffic conditions. In this paper, we create and use a dataset by using a customised version of the MetaDrive simulator capable of collecting both human and AI driving data. Then we simulate several types of intrusions while driving: denial of service, spoofing and replay attacks. As a final step, we use the generated dataset to evaluate the CAHOOT algorithm by using several machine learning methods. The results show that CAHOOT is extremely reliable in detecting intrusions. |
BibTeX:
@INPROCEEDINGS{Micale2022,
author={Davide Micale and Gianpiero Costantino and Ilaria Matteucci and Florian Fenzl and Roland Rieke and Giuseppe Patane},
booktitle={},
title={CAHOOT: A Context-Aware veHicular intrusiOn detectiOn sysTem},
year={2022},
month={November},
volume={},
number={},
pages={},
doi={10.1109/TrustCom56396.2022.00168}}
|
|
Clemens Arzt, Steven Kleemann, Christian Plappert, Roland Rieke, and Daniel Zelle Datenverarbeitung und Cybersicherheit in der Fahrzeugautomatisierung - Rechtliche und technische Anforderungen im Verbund, MMR-Beilage, MultiMedia und Recht - Beilage, Heft 7 (Seite 593-614), C.H.Beck, 2022 |
| Abstract: Der Beitrag ertert ausf�hrlich die neue Rechtslage vor dem Hintergrund des nationalen und europäischen Datenschutzrechts und den Vorgaben der dazugehigen UNECE-Regelungen. Von besonderem Interesse sind in diesem Zusammenhang der neue § 1g StVG und die in der AFGBV enthaltenen Regelungen f�r den Betrieb eines digitalen Datenspeichers sowie die Anforderungen an die Sicherheit im Bereich der Informationstechnologie bei Datenspeicherung und Daten�bermittlung automatisierter Kraftfahrzeuge. Die hier als relevant identifizierten UNECE-Regelungen 155 (Cybersicherheit) und 156 (Software-Updates) werden in Folge dieser Neuregelung k�nftig einen noch wichtigeren Stellenwert im Automobilbereich einnehmen. Die an die rechtlichen Ausf�hrungen anschließende technische Analyse in diesem Beitrag leitet IT- und Datensicherheitsanforderungen sowie beispielhafte Maßnahmen zur wirkungsvollen Umsetzung ab und vergleicht diese mit den Maßgaben der einschlägigen UNECE-Regelungen. Dabei wird aufgezeigt, welche technischen Maßnahmen erforderlich sind, um diesen Anforderungen gerecht zu werden. Die hieraus abgeleiteten technischen Maßnahmen nehmen Bezug auf die rechtlichen Regelungen und ermlichen dadurch einen belastbaren Abgleich von Technik und Recht. |
BibTeX:
@INPROCEEDINGS{Arzt2022,
author={Clemens Arzt and Steven Kleemann and Christian Plappert and Roland Rieke and Daniel Zelle},
booktitle={MMR-Beilage, MultiMedia und Recht - Beilage, 593},
title={Datenverarbeitung und Cybersicherheit in der Fahrzeugautomatisierung - Rechtliche und technische Anforderungen im Verbund},
year={2022},
month={July},
volume={2022},
number={7},
pages={593-614},
url = {https://beck-online.beck.de/Bcid/Y-300-Z-MMR-BEIL-B-2022-S-593-N-1}}
|
|
Lucas Buschlinger, Roland Rieke, Sanat Sarda, and Christoph Krauß, Decision Tree-Based Rule Derivation for Intrusion Detection in Safety-Critical Automotive Systems, PDP2022, virtual Valladolid Spain, March 09-11 2022 |
| Abstract: Intrusion Detection Systems (IDSs) are being introduced into safety-critical systems such as connected vehicles. Since the behavior and effectiveness of measures are validated before approval, the decisions made by an IDS are required to be traceable and the IDS also needs to work efficiently on resource-constrained embedded systems. These requirements complicate the direct use of Machine Learning (ML) approaches in IDS design. In this paper, we propose an approach to using ML to generate rules for an efficient rule-based IDS like Snort. Our approach eases the time-consuming and difficult process of creating a rule set. We use decision trees to generate rules that can be used by experts as a basis for creating a rule set for a specific safety-critical use case. In addition, we use long short-term memory methods to circumvent the problem of limited training data availability, a common limitation in safety-critical systems. Our implementation and evaluation shows the feasibility of our approach to derive specific IDS rules for such systems. |
BibTeX:
@INPROCEEDINGS{Buschlinger2022,
author={Lucas Buschlinger and Roland Rieke and Sanat Sarda and Christoph Krau{\ss}},
booktitle={2022 30th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={Decision Tree-Based Rule Derivation for Intrusion Detection in Safety-Critical Automotive Systems},
year={2022},
month={March},
volume={},
number={},
pages={246-254},
doi={10.1109/PDP55904.2022.00046}}
|
|
Christian Plappert, Florian Fenzl, Roland Rieke, Ilaria Matteucci, Gianpiero Costantino, and Marco De Vincenzi, SECPAT: Security Patterns for Resilient Automotive E/E Architectures, PDP2022, virtual Valladolid Spain, March 09-11 2022 |
| Abstract: Automated driving requires increasing networking of vehicles, which in turn broadens their attack surface. In this paper, we describe several security design patterns that target critical steps in automotive attack chains and mitigate their consequences. These patterns enable the detection of anomalies in the firmware when booting, detect anomalies in the communication in the vehicle, prevent unauthorized control units from successfully transmitting messages, offer a way of transmitting security-related events within a vehicle network and reporting them to units external to the vehicle, and ensure that communication in the vehicle is secure. Using the example of a future high-level Electrical / Electronic (E / E) architecture, we also describe how these security design patterns can be used to become aware of the current attack situation and how to react to it. |
BibTeX:
@INPROCEEDINGS{Plappert2022,
author={Christian Plappert and Florian Fenzl and Roland Rieke and Ilaria Matteucci and Gianpiero Costantino and Marco De Vincenzi},
booktitle={2022 30th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={SECPAT: Security Patterns for Resilient Automotive E/E Architectures},
year={2022},
month={March},
volume={},
number={},
pages={255-264},
doi={10.1109/PDP55904.2022.00047}}
|
|
Daniel Zelle, Christian Plappert, Roland Rieke, Dirk Scheuermann, and Christoph Krauß, ThreatSurf: A method for automated Threat Surface assessment in automotive cybersecurity engineering, Elsevier journal: Microprocessors and Microsystems: Embedded Hardware Design (MICPRO), 2022 |
| Abstract: Connected smart cars enable new attacks that may have serious consequences. Thus, the development of new cars must follow a cybersecurity engineering process including a Threat Analysis and Risk Assessment (TARA). The attack surface assessment is a central aspect of a TARA. In this paper, we introduce a concrete approach for attack surface assessment following the steps asset identification, threat scenario identification, attack path analysis, and attack feasibility rating of a TARA compliant to ISO/SAE DIS 21434 and an approach to automatize them. We define a generic reference architecture and assets constituting the attack surface, attack building blocks with associated feasibility rating, and a method for automated generation and rating of attack paths using the attack building blocks and attack feasibility. Our exemplary application of the automated attack surface assessment on several threats from the UN regulation no. 155 shows the feasibility of our approach. |
BibTeX:
@article{Zelle2022,
title = {ThreatSurf: A method for automated Threat Surface assessment in automotive cybersecurity engineering},
author={Daniel Zelle and Christian Plappert and Roland Rieke and Dirk Scheuermann and Christoph Krau{\ss}},
journal = {Microprocessors and Microsystems},
volume = {90},
pages = {104461},
year = {2022},
issn = {0141-9331},
doi = {10.1016/j.micpro.2022.104461},
url = {https://www.sciencedirect.com/science/article/pii/S0141933122000321},
}
|
|
Yannick Chavalier, Florian Fenzl, Maxim Kolomeets, Roland Rieke, Andrey Chechulin, and Christoph Krauß, Cyberattack detection in vehicles using characteristic functions, artificial neural networks and visual analysis, Journal of Informatics and Automation (SPIIRAS Proceedings) |
| Abstract: The connectivity of autonomous vehicles induces new attack surfaces and thus the demand for sophisticated cybersecurity management. Thus, it is important to ensure that in-vehicle network monitoring includes the ability to accurately detect intrusive behavior and analyze cyberattacks from vehicle data and vehicle logs in a privacy-friendly manner. For this purpose, we describe and evaluate a method that utilizes characteristic functions and compare it with an approach based on artificial neural networks. Visual analysis of the respective event streams complements the evaluation. Although the characteristic functions method is an order of magnitude faster, the accuracy of the results obtained is at least comparable to those obtained with the artificial neural network. Thus, this method is an interesting option for implementation in in-vehicle embedded systems. An important aspect for the usage of the analysis methods within a cybersecurity framework is the explainability of the detection results. |
BibTeX:
@article{Chevalier2021,
title={Cyberattack detection in vehicles using characteristic functions, artificial neural networks, and visual analysis},
volume={20},
url={http://ia.spcras.ru/index.php/sp/article/view/15028},
DOI={10.15622/ia.20.4.4},
number={4},
journal={Informatics and Automation},
author={Chevalier, Yannick and Fenzl, Florian and Kolomeets, Maxim and Rieke, Roland and Chechulin, Andrey and Krau{\ss}, Christoph},
year={2021},
month={Aug.},
pages={845-868}
}
|
|
Florian Fenzl, Roland Rieke, and Andreas Dominik, In-vehicle detection of targeted CAN bus attacks, ARES2021 |
| Abstract: Most vehicles use the controller area network bus for communication between their components. Attackers who have already penetrated the in-vehicle network often utilize this bus in order to take control of safety-relevant components of the vehicle. Such targeted attack scenarios are often hard to detect by network intrusion detection systems because the specific payload is usually not contained within their training data sets. In this work, we describe an intrusion detection system that uses decision trees that have been modelled through genetic programming. We evaluate the advantages and disadvantages of this approach compared to artificial neural networks and rule-based approaches. For this, we model and simulate specific targeted attacks as well as several types of intrusions described in the literature. The results show that the genetic programming approach is well suited to identify intrusions with respect to complex relationships between sensor values which we consider important for the classification of specific targeted attacks. However, the system is less efficient for the classification of other types of attacks which are better identified by the alternative methods in our evaluation. Further research could thus consider hybrid approaches. |
BibTeX:
@inproceedings{Fenzl2021,
author = {Fenzl, Florian and Rieke, Roland and Dominik, Andreas},
title = {In-Vehicle Detection of Targeted CAN Bus Attacks},
year = {2021},
isbn = {9781450390514},
publisher = {Association for Computing Machinery},
address = {New York, NY, USA},
url = {https://doi.org/10.1145/3465481.3465755},
doi = {10.1145/3465481.3465755},
abstract = { Most vehicles use the controller area network bus for communication between their
components. Attackers who have already penetrated the in-vehicle network often utilize
this bus in order to take control of safety-relevant components of the vehicle. Such
targeted attack scenarios are often hard to detect by network intrusion detection
systems because the specific payload is usually not contained within their training
data sets. In this work, we describe an intrusion detection system that uses decision
trees that have been modelled through genetic programming. We evaluate the advantages
and disadvantages of this approach compared to artificial neural networks and rule-based
approaches. For this, we model and simulate specific targeted attacks as well as several
types of intrusions described in the literature. The results show that the genetic
programming approach is well suited to identify intrusions with respect to complex
relationships between sensor values which we consider important for the classification
of specific targeted attacks. However, the system is less efficient for the classification
of other types of attacks which are better identified by the alternative methods in
our evaluation. Further research could thus consider hybrid approaches.},
booktitle = {The 16th International Conference on Availability, Reliability and Security},
articleno = {32},
numpages = {7},
keywords = {Controller area network security, Machine learning, Intrusion detection, Security monitoring, Automotive security, Anomaly detection, Genetic Programming},
location = {Vienna, Austria},
series = {ARES 2021}
}
|
|
Christian Plappert, Daniel Zelle, Henry Gadacz, Roland Rieke, Dirk Scheuermann, and
Christoph Krauß, Attack Surface Assessment for Cybersecurity Engineering in the Automotive Domain, PDP2021, Valladolid Spain, March 10-12 2021 |
| Abstract: Connected smart cars enable new attacks which may have serious consequences. Thus, the development of new cars must follow a cybersecurity engineering process as defined for example in ISO/SAE 21434. A central part of such a process is the threat and risk assessment including an attack feasibility rating. We present an attack surface assessment with focus on the attack feasibility rating compliant to ISO/SAE 21434. We introduce a reference architecture with assets constituting the attack surface, the attack feasibility rating for these assets, and the application of this rating on typical use cases. The attack feasibility rating assigns attacks and assets to an evaluation of the attacker dimensions and the feasibility of attacks derived from it. We show on sample use cases how this rating can be used to assess the feasibility of an entire attack path. The attack feasibility rating can be used as a building block in a threat and risk assessment according to ISO/SAE 21434. |
BibTeX:
@INPROCEEDINGS{Plappert2021,
author={Plappert, Christian and Zelle, Daniel and Gadacz, Henry and Rieke, Roland and Scheuermann, Dirk and Krauß, Christoph},
booktitle={2021 29th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP)},
title={Attack Surface Assessment for Cybersecurity Engineering in the Automotive Domain},
year={2021},
volume={},
number={},
pages={266-275},
doi={10.1109/PDP52278.2021.00050}}
|
| Florian Fenzl, Roland Rieke, Yannick Chevalier, Andreas Dominik, and Igor Kotenko, Continuous Fields: Enhanced In-Vehicle Anomaly Detection using Machine Learning Models, Elsevier Journal: Simulation Modelling Practice and Theory, 2020 |
| Abstract: The attack surface of a modern vehicle increases with its connectivity. A strategy to prevent attacks or at least to identify such attacks and to mitigate their effects is therefore imperative. The detection of indications for intrusive behavior in an in-vehicle network is an important aspect of a holistic security concept. The structure of the payload of in-vehicle messages with respect to the encoded sensor values is in general confidential. Therefore, most researchers consider the structure of the in-vehicle messages to be bit- or byte-fields. However, this may hide anomalies which are characterized by correlations between sensor values transferred by the in-vehicle messages. In this work, we evaluate the influence of accuracy of the model of the payload structure with respect to the actual sensor values on the results of different intrusion detection methods. In particular, we analyze if an improved alignment is helpful to detect anomalies introduced by stealthy intrusions. In order to cover conceptually different modeling and reasoning techniques, we adapted a deep learning approach as well as a characteristic functions based intrusion detection approach to utilize such message streams. An important aspect is that the explainability of the results is better compared to deep learning systems. We further developed a set of test vectors based on log files of a vehicle enriched by different intrusions. In particular, we included simulations of stealthy intrusions which mask certain sensor values within the respective messages. The effectiveness of the developed methods is demonstrated by various experiments. |
BibTeX:
@article{Fenzl2020,
author = "Florian Fenzl and Roland Rieke and Yannick Chevalier and Andreas Dominik and Igor Kotenko",
title = "Continuous Fields: Enhanced In-Vehicle Anomaly Detection using Machine Learning Models",
journal = "Simulation Modelling Practice and Theory",
volume = "105",
pages = "102143",
year = "2020",
issn = "1569-190X",
doi = "https://doi.org/10.1016/j.simpat.2020.102143",
url = "http://www.sciencedirect.com/science/article/pii/S1569190X20300824",
keywords = "Controller area network security, Intrusion detection, Anomaly detection, Machine learning, Automotive security, Security monitoring",
}
|
| Daniel Zelle, Roland Rieke,Christian Plappert, Christoph Krauß, Dmitry Levshun, and Andrey Chechulin (2020), SEPAD - Security Evaluation Platform for Autonomous Driving, PDP2020, Västerås, Sweden, March 11-13, 2020 |
| Abstract: The development and evaluation of security solutions for autonomous vehicles is a challenging task. Many researchers have no access to real vehicles to implement and test their solutions. In addition, vehicle E/E architectures of different brands or even model series of one car manufacturer differ significantly. Also, vehicles may be the source of physical hazards, e.g., an exploding airbag. To enable researchers to develop, implement, and evaluate new security solutions for autonomous vehicles, we propose a new security evaluation platform called SEPAD and a dedicated development process for testing security mechanisms with it. SEPAD allows to model realistic E/E architectures where the developed security solutions can be integrated and evaluated without causing safety risks for the researcher or other road users. |
BibTeX:
@InProceedings{Zelle2020,
author={D. {Zelle} and R. {Rieke} and C. {Plappert} and C. {Krauß} and
D. {Levshun} and A. {Chechulin}},
booktitle={2020 28th Euromicro International Conference on Parallel,
Distributed and Network-Based Processing (PDP)},
title={SEPAD - Security Evaluation Platform for Autonomous Driving},
year={2020},
volume={},
number={},
pages={413-420},
abstract={The development and evaluation of security solutions for
autonomous vehicles is a challenging task. Many researchers have no
access to real vehicles to implement and test their solutions. In
addition, vehicle E/E architectures of different brands or even model
series of one car manufacturer differ significantly. Also, vehicles may
be the source of physical hazards, e.g., an exploding airbag. To enable
researchers to develop, implement, and evaluate new security solutions
for autonomous vehicles, we propose a new security evaluation platform
called SEPAD and a dedicated development process for testing security
mechanisms with it. SEPAD allows to model realistic E/E architectures
where the developed security solutions can be integrated and evaluated
without causing safety risks for the researcher or other road users.},
keywords={Security;Autonomous vehicles;Protocols;Computer
architecture;Automotive engineering;Sensors;Automobiles;automotive
security;evaluation platform;autonomous driving;intrusion
detection;trusted computing;secure in-vehicle protocols},
doi={10.1109/PDP50117.2020.00070},
ISSN={2377-5750},
month={March},
}
|
| Yannick Chevalier, Roland Rieke, Florian Fenzl, Andrey Chechulin, and Igor Kotenko (2019), ECU-Secure: Characteristic Functions for In-Vehicle Intrusion Detection, IDC2019, St. Petersburg, Russia, October 7-9, 2019 (Springer SCI, volume 868) |
| Abstract: Growing connectivity of vehicles induces increasing attack surfaces and thus the demand for a sophisticated security strategy. One part of such a strategy is to accurately detect intrusive behavior in an in-vehicle network. Therefore, we built a log analyzer in C that focused on payload bytes having either a small set of different values or a small set of possible changes. While being an order of magnitude faster, the accuracy of the results obtained is at least comparable with results obtained using standard machine learning techniques. These features make this approach an interesting option for implementation within in-vehicle embedded systems. Another important aspect is that the explainability of the results is better compared to deep learning systems. |
BibTeX:
@InProceedings{Chevalier2019,
author = {Yannick Chevalier and Roland Rieke and Florian Fenzl and Andrey Chechulin and Igor V. Kotenko},
editor = {Igor V. Kotenko and Costin Badica and Vasily Desnitsky and Didier El Baz and Mirjana Ivanovic},
title="ECU-Secure: Characteristic Functions for In-Vehicle Intrusion Detection",
booktitle="Intelligent Distributed Computing XIII",
series = {Studies in Computational Intelligence},
volume = {868},
publisher = {Springer},
year = {2020},
address="Cham",
pages={495--504},
doi = {10.1007/978-3-030-32258-8\_58},
isbn="978-3-030-32258-8"
}
|
| Daniel Zelle, Roland Rieke, and Christoph Krauß (2019), Security Test Platform for Autonomous Driving, 3. ACM COMPUTER SCIENCE IN CARS SYMPOSIUM (CSCS 2019) |
BibTeX:
@techreport{CSCS2019,
author = {Daniel Zelle and Roland Rieke and Christoph Krau\ss{}},
year = {2019},
month = {October},
title = {Security Test Platform for Autonomous Driving},
url = {https://cscs19.cispa.saarland/files/cscs19_camera_ready/19_TestbedSAD.pdf},
language = {english},
institution = {3. ACM COMPUTER SCIENCE IN CARS SYMPOSIUM (CSCS 2019)}
}
|
| Ivo Berger, Roland Rieke, Maxim Kolomeets, Andrey Chechulin, and Igor Kotenko (2018), Comparative study of machine learning methods for in-vehicle intrusion detection, Computer Security. ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, September 6-7, 2018, Revised Selected Papers (Springer LNCS 11387) |
| Abstract: An increasing amount of cyber-physical systems within modern cars, such as sensors, actuators, and their electronic control units are connected by in-vehicle networks and these in turn are connected to the evolving Internet of vehicles in order to provide ``smart'' features such as automatic driving assistance. The controller area network bus is commonly used to exchange data between different components of the vehicle, including safety critical systems as well as infotainment. As every connected controller broadcasts its data on this bus it is very susceptible to intrusion attacks which are enabled by the high interconnectivity and can be executed remotely using the Internet connection. This paper aims to evaluate relatively simple machine learning methods as well as deep learning methods and develop adaptations to the automotive domain in order to determine the validity of the observed data stream and identify potential security threats. |
BibTeX:
@InProceedings{Berger2019,
author="Berger, Ivo
and Rieke, Roland
and Kolomeets, Maxim
and Chechulin, Andrey
and Kotenko, Igor",
editor="Katsikas, Sokratis K.
and Cuppens, Fr{\'e}d{\'e}ric
and Cuppens, Nora
and Lambrinoudakis, Costas
and Ant{\'o}n, Annie
and Gritzalis, Stefanos
and Mylopoulos, John
and Kalloniatis, Christos",
title="Comparative Study of Machine Learning Methods for In-Vehicle Intrusion Detection",
booktitle="Computer Security. ESORICS 2018 International Workshops, CyberICPS 2018 and SECPRE 2018, Barcelona, Spain, September 6-7, 2018, Revised Selected Papers",
year="2019",
publisher="Springer",
address="Cham",
pages="85--101",
abstract="An increasing amount of cyber-physical systems within modern cars, such as sensors, actuators, and their electronic control units are connected by in-vehicle networks and these in turn are connected to the evolving Internet of vehicles in order to provide ``smart'' features such as automatic driving assistance. The controller area network bus is commonly used to exchange data between different components of the vehicle, including safety critical systems as well as infotainment. As every connected controller broadcasts its data on this bus it is very susceptible to intrusion attacks which are enabled by the high interconnectivity and can be executed remotely using the Internet connection. This paper aims to evaluate relatively simple machine learning methods as well as deep learning methods and develop adaptations to the automotive domain in order to determine the validity of the observed data stream and identify potential security threats.",
isbn="978-3-030-12786-2",
series = {Lecture Notes in Computer Science},
volume = {11387},
doi = {10.1007/978-3-030-12786-2_6},
}
|
| Roland Rieke, Marc Seidemann, Elise Kengni Talla, Daniel Zelle, and Bernhard Seeger (2017), Behavior Analysis for Safety and Security in Automotive Systems, The 25th Euromicro International Conference on Parallel, Distributed and Network-based Computing (PDP 2017) |
| Abstract: The connection of automotive systems with other systems such as road-side units, other vehicles, and various servers in the Internet opens up new ways for attackers to remotely access safety relevant subsystems within connected cars. The security of connected cars and the whole vehicular ecosystem is thus of utmost importance for consumer trust and acceptance of this emerging technology. This paper describes an approach for on-board detection of unanticipated sequences of events in order to identify suspicious activities. The results show that this approach is fast enough for in-vehicle application at runtime. Several behavior models and synchronization strategies are analyzed in order to narrow down suspicious sequences of events to be sent in a privacy respecting way to a global security operations center for further in-depth analysis. |
BibTeX:
@INPROCEEDINGS{pdp2017,
booktitle={Parallel, Distributed and Network-Based Processing (PDP), 2017 25nd Euromicro International Conference on},
author={Roland Rieke and Marc Seidemann and Elise Kengni Talla and Daniel Zelle and Bernhard Seeger},
title={Behavior Analysis for Safety and Security in Automotive Systems},
year={2017},
month={Mar},
pages={381-385},
keywords={automotive security; connected car; predictive security analysis;
security modeling and simulation; security monitoring;
complex event processing; process discovery},
doi={10.1109/PDP.2017.67},
url={http://ieeexplore.ieee.org/document/7912675/},
publisher = {IEEE Computer Society},
}
|
| Andreas Fuchs and Roland Rieke (2010), Identification of Security Requirements in Systems of Systems by Functional Security Analysis, In Architecting Dependable Systems VII, (Springer LNCS 6420) |
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning however raise severe concerns to security issues. Here, we address the security requirements elicitation step in the security engineering process for such systems of systems. The method comprises the tracing down of functional dependencies over system component boundaries right onto the origin of information as a functional flow graph. Based on this graph, we systematically deduce comprehensive sets of formally defined authenticity requirements for the given security and dependability objectives. The proposed method thereby avoids premature assumptions on the security architecture's structure as well as the means by which it is realised. Furthermore, a tool-assisted approach that follows the presented methodology is described. |
BibTeX:
@incollection{fuchs:rieke:2010,
author = {Andreas Fuchs and Roland Rieke},
title = {{Identification of Security Requirements in Systems of Systems by Functional Security Analysis}},
booktitle = {Architecting Dependable Systems VII},
editor = {Antonio Casimiro and Rogério de Lemos and Cristina Gacek},
publisher = {Springer},
series = {Lecture Notes in Computer Science},
volume = {6420},
year = {2010},
pages = {74--96},
doi={10.1007/978-3-642-17245-8_4},
url={http://dx.doi.org/10.1007/978-3-642-17245-8_4},
isbn = {978-3-642-17244-1}
}
|
| Andreas Fuchs and Roland Rieke (2010), Identification of Security Requirements for Vehicular Communication Systems, 2010 CAST-Workshop on Mobile Security for Intelligent Cars (EVITA project workshop) |
BibTeX:
@inproceedings{talks-CAST:2010,
editor = {Olaf Henniger},
booktitle = {Presentation slides from the EVITA project workshop},
author = {Andreas Fuchs and Roland Rieke},
title = {Identification of Security Requirements for Vehicular Communication Systems},
institution = {EVITA European project},
type = {Deliverable},
number = {D1.2.5.1},
year = {2010},
month= {July},
note = {CAST-Workshop on Mobile Security for Intelligent Cars, Darmstadt, Germany},
url = {http://evita-project.org/Publications/EVITAD1.2.5.1.pdf}
}
|
|
Alastair Ruddle, David Ward, Benjamin Weyl, Sabir Idrees,
Yves Roudier, Michael Friedewald, Timo Leimbach, Andreas
Fuchs, Sigrid Gürgens, Olaf Henniger, Roland Rieke,
Matthias Ritscher, Henrik Broberg, Ludovic Apvrille, Renaud
Pacalet, and Gabriel Pedroza (2009) Security requirements for automotive on-board networks based on dark-side scenarios, EVITA Deliverable D2.3 |
| Abstract: The objective of the EVITA project is to design, verify, and prototype an architecture for automotive on-board networks where security-relevant components are protected against tampering and sensitive data are protected against compromise. Thus, EVITA will provide a basis for the secure deployment of electronic safety aids based on vehicle-to-vehicle and vehicle-to-infrastructure communication. A key activity for the EVITA project is the capture of security requirements for the secure system architecture and associated software and hardware components based on a set of use cases and an investigation of security threat scenarios (dark-side scenarios). This document outlines the processes used to identify and evaluate security requirements, and details the results of their application to automotive on-board networks. It provides input to the secure on-board architecture design. |
BibTeX:
@techreport{other-evita-d2.3,
author = {Alastair Ruddle and David Ward and Benjamin Weyl and Sabir Idrees
and Yves Roudier and Michael Friedewald and Timo Leimbach and Andreas
Fuchs and Sigrid G\"urgens and Olaf Henniger and Roland Rieke and
Matthias Ritscher and Henrik Broberg and Ludovic Apvrille and Renaud
Pacalet and Gabriel Pedroza},
title = {Security requirements for automotive on-board networks based on dark-side
scenarios},
institution = {EVITA project},
year = {2009},
type = {{EVITA Deliverable D2.3}},
url = {http://evita-project.org/deliverables.html}
}
|
|
Christophe Jouvray, Antonio Kung, Michel Sall,
Andreas Fuchs, Sigrid Gürgens, Roland Rieke
(2009) Security and trust model, EVITA Deliverable D3.1 |
| Abstract: The objective of the EVITA project is to design, verify, and prototype an architecture for automotive on-board networks where security-relevant components are protected against tampering and sensitive data are protected against compromise. Thus, EVITA will provide a basis for the secure deployment of electronic safety aids based on vehicle-to-vehicle and vehicle-to-infrastructure communication. Designing a system respecting the criteria of security and trust is a complex task. Security will cover various aspects such as dependability, integrity, authenticity, or even privacy. It is thus possible to have confidence in a system where evidence is provided to the user. To do this, taking into account security issues should begin early in the product life cycle. Currently, model driven approaches are used in application design. Model oriented approaches must be adjusted to take into account the security mechanisms. This document analyzes different approaches to security architecture models and specifies a suitable security and trust model for automotive on-board networks. Two main solutions are proposed to adapt model approaches. The first one concerns directly the model driven engineering by introducing all needed concepts into a model. The second solution proposes a formal method for the refinement of security properties. High level properties specified within a platform-independent model can be refined to properties required by certain security mechanisms which in turn reflect the platform-specific architecture chosen. |
BibTeX:
@techreport{other-evita-d3.1,
author = {Christophe Jouvray and Antonio Kung and Michel Sall and Andreas
Fuchs and Sigrid G\"urgens and Roland Rieke},
title = {Security and trust model},
institution = {EVITA project},
year = {2009},
type = {{EVITA Deliverable D3.1}},
url = {http://evita-project.org/deliverables.html}
}
|
| Andreas Fuchs and Roland Rieke (2009), Identification of authenticity requirements in systems of systems by functional security analysis, In Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume. |
| Abstract: Cooperating systems typically base decisions on information from their own components as well as on input from other systems. Safety critical decisions based on cooperative reasoning, such as automatic emergency braking of a vehicle, raise severe concerns to security issues. In this paper we address the security engineering process for such systems of systems. The presented authenticity requirements elicitation method is based on functional dependency analysis. It comprises the tracing down of functional dependencies over system boundaries right onto the origin of information. A dependency graph with a safety critical function as root and the origins of decision relevant information as leaves is used to deduce a set of authenticity requirements. This set is comprehensive and defines the maximal set of authenticity requirements from the given functional dependencies. Furthermore, the proposed method avoids premature assumptions on the architectural structure and mechanisms to implement security measures. |
BibTeX:
@inproceedings{fuchs:rieke:2009,
author = {Andreas Fuchs and Roland Rieke},
title = {Identification of authenticity requirements in systems of systems by functional security analysis},
booktitle = {Workshop on Architecting Dependable Systems (WADS 2009), in Proceedings of the 2009 IEEE/IFIP Conference on Dependable Systems and Networks, Supplemental Volume},
year = {2009},
pages={E29-E34},
}
|